Configuration
EnableIdpInitiatedSignonPage
| Applies to |
|---|
| Windows Server 2016 |
| Windows Server 2019 |
| Windows Server 2022 |
You can use this feature to test sign-on to the configured Relying Party Trusts. By default this feature is disabled (except on Windows Server 2012), but you can check the status with the following PowerShell command:
Get-AdfsProperties | fl *idpinitiatedsignon*
To enable this feature, use the following PowerShell command:
Set-AdfsProperties -EnableIdpInitiatedSignonPage $true
To check the operation of the ADFS plugin, you can open the link in the browser and perform primary authentication:
https://{{yourDomainName}}/adfs/ls/idpinitiatedsignon.aspx
Authentication Policies
| Applies to |
|---|
| Windows Server 2012 R2 |
| Windows Server 2016 |
| Windows Server 2019 |
| Windows Server 2022 |
Windows Server 2016/2019/2022
Open the ADFS management console and navigate to the Authentication Methods section of your ADFS instance under AD FS > Service. You should already see the ADFS plugin inline for IDComplete listed under Multi-factor Authentication Methods, but if not, click Edit or "Edit Multi-factor Authentication Methods..." on the right hand side:

From here, ensure that the ADFS plugin inline for IDComplete checkbox is enabled:

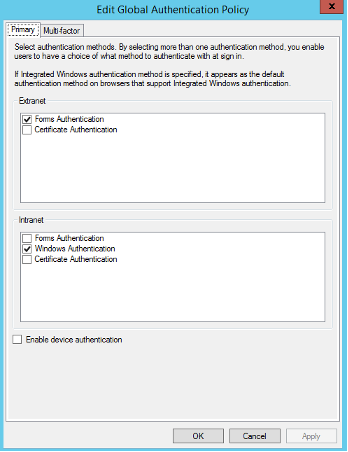
Finally, ensure that the Primary tab has the following options enabled:

Next, you can apply the policy to individual Relying Party Trusts. Navigate to Relying Party Trusts and select the one you want to edit, then click "Edit Access Control Policy..." on the right hand side:

Now, simply create or choose a policy that will require users to use MFA and click Apply.

Windows Server 2012
You can either set policies globally for all Relying Party Trusts, or on an individual basis. For global settings, open the ADFS management console and navigate to the Authentication Policies section of your ADFS instance and click the Edit button under Multi-factor Authentication > Global Settings:
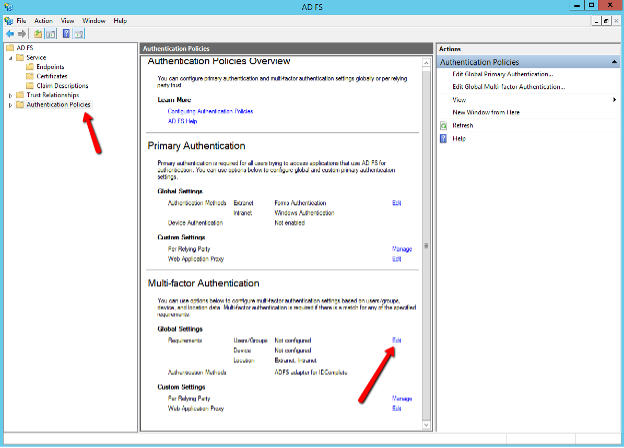
Check following parameters and enable them if they are disabled:
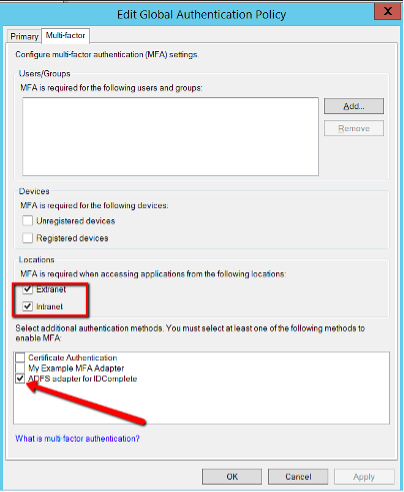
You can also set the policies individually. Navigate to Authentication Policies > Per Relying Party Trust and either right-click the relevant Relying Party Trust and choosing "Edit Custom Multi-factor Authentication..." or clicking the same option on the right-side menu.

Allow Additional Authentication as Primary
| Applies to |
|---|
| Windows Server 2019 |
| Windows Server 2022 |
If you are running ADFS on Windows Server 2019+, you can take advantage of the ability to use additional authentication methods as a first factor, which could potentially eliminate the need for passwords entirely. More information can be found on the Microsoft website.
To enable this behavior, you can open a PowerShell window and use the following command:
Set-AdfsGlobalAuthenticationPolicy -AllowAdditionalAuthenticationAsPrimary $true
You can also access this setting in the AD FS Management console by navigating to Service > Authentication Methods and then clicking "Edit Primary Authentication Methods..." on the right-hand side. Click the checkbox marked Allow additional authentication providers as primary.

Apply the changes, then open the dialog again and ensure that only the ADFS plugin inline for IDComplete is checked for Extranet and Intranet locations:

HTTP Response Headers
| Applies to |
|---|
| Windows Server 2019 |
| Windows Server 2022 |
authID loads the plugin UI via IFrame. However, certain versions prevent content from being loaded due to a default Content Security Policy. You will need to modify the CSP to allow authID's origin. Check your existing policy with the following PowerShell command:
Get-AdfsResponseHeaders
Copy the content of the Content-Security-Policy directive, and add frame-src: https://id.authid.ai; to the value. Use the following command to propagate the changes:
Set-AdfsResponseHeaders -SetHeaderName "Content-Security-Policy" -SetHeaderValue "...; frame-src: https://id.authid.ai; ..."
Enable Paginated Sign-in
| Applies to |
|---|
| Windows Server 2012 R2 |
| Windows Server 2016 |
| Windows Server 2019 |
| Windows Server 2022 |
ADFS supports a new experience for logins that involves paginated sign in. You can enable the paginated experience using the following PowerShell command:
Set-AdfsGlobalAuthenticationPolicy -EnablePaginatedAuthenticationPages $true
More information can be found on the Microsoft website.