Authentication Transaction
V.1
authID Verified Transactions enable organizations to strengthen security and protect their users using Biometric Authentication transaction context to improve security and compliance further.
Before requesting that an Authentication Transaction be generated, the authID Account must have a biometric or passwordless credential enrolled.
Integration can invoke user verification when user identity confirmation is required, such as at login or during any privileged action, effectively implementing a zero-trust policy.
API Sequence
The overall sequence of API calls and other actions the integration has to follow is straightforward and almost identical to Proof (IDV) transactions and other enrollment-type transactions.
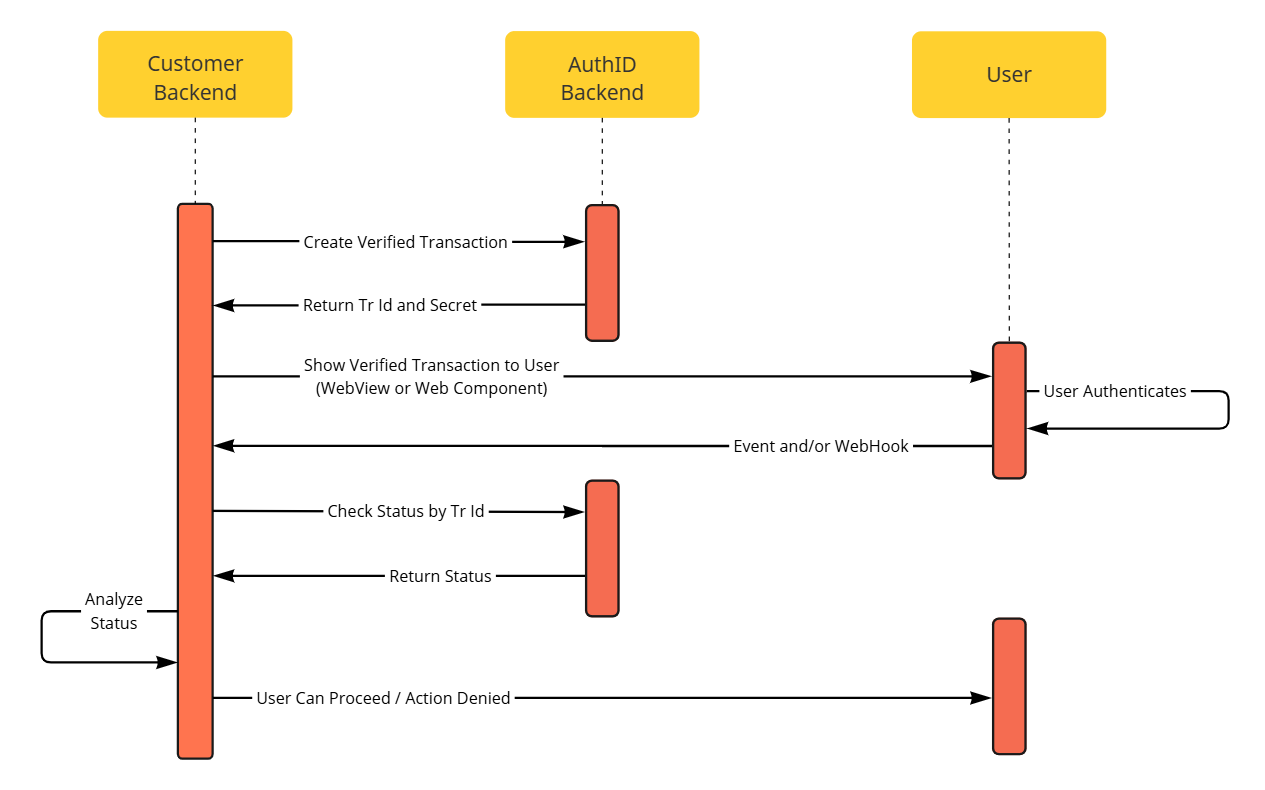
API Sequence.
Create Authentication Transaction
To begin the process of authenticating the user's identity using authID account credentials and attributes, the new transaction must be requested via API using the New Transactions Endpoint.
The example of POST body:
{
"AccountNumber": "AccountV2",
"Timeout": 3600,
"ConfirmationPolicy": {
"TransportType": 0,
"CredentialType": 1,
"BioPolicy": {
"CheckLiveness": true
}
},
"Name": "Verify_Identity"
}Transaction Template Name
The Name parameters are required and must refer to the existing configured transaction template. Every Customer Sandbox/Teanant comes with at least one named template "Verify_Identity"
New templates and template customization can be requested from authID support and include multiple elements such as color schemes, email branding, SMS content, logos, and more.
Confirmation Policy
Confirmation Policy object is required, developers must construct policies by including the Transport Type, Credential Type, and additional items depending on the Credential Type specified for the policy.
"ConfirmationPolicy": {
"TransportType": 2,
"CredentialType": 4
}
Effect of Selected Policy on User Experience and SecurityPlease visit Verified Confirmation Policies page for more details.
The Credential Types
| CredentialType | Description |
|---|---|
| 0 | Basic (web link only, no credential) |
| 1 | Biometrics |
| 2 | OTP |
| 4 | FIDO |
The Transport Types
| TransportType | Description |
|---|---|
| 0 | Embedded \ Inline |
| 1 | SMS |
| 2 |
Using TransportType 0 returns a TransactionId and a OneTimeSecret. Save these values from the response and use them to display the UI to the user. Example response body:
{
"TransactionId": "c4f2014f-9c43-665a-af52-a78d13da0503",
"OneTimeSecret": "Uw6ZwefA5FEBV9furMYlvFBs"
}Display the User Interface
Use the values from the previous step to display the Embedded Capture Experience to the user.
The other options for TransportType parameter usage are described in the Out-of-band Transactions section.
Wait for the User to Complete Authentication
When the user completes Authentication, the status changes from 0 - Pending to another status. Refer to the Transaction Statuses section for more details.
Authentication Success StatusOnly 1 - Accepted signifies "authentication success", any other status must be treated as "authentication failed"
The application has several ways to detect when the status changes.
- Periodic polling of the backend for Enrollment operation status changes using Transaction Status Endpoint
- Embedded Integration can listen to Web Component Events for web integration or to JavaScript bridge events for WebView integration. The UI emits the signal that the user has reached the "final page" of the experience.
Please refer to the Web Component Events section for more details.
The best strategy from both a UX transition reaction time and system load perspective is to:
- Listen to events from the Web Component / WebView.
- When the user reaches the final page, pass the signal from your application frontend to your application's backend.
- Confirm the status change via the backend Transaction Status Endpoint.
- As a backup, poll status changes periodically using Transaction Status Endpoint, for example, once every 5 seconds.
Both Out-of-band and Embedded integrations can use Webhook to receive notifications when the status changes. Note that webhooks are not queued and do not have guaranteed delivery, so the periodic polling backup strategy still applies.
Include Geofencing Data (Optional)
To provide additional transaction context, you can include geolocation and device metadata at the moment of confirming the transaction. This optional data is useful for internal audits, future policy decisions, or security analytics.
This information is passed in the Geofencing object and can be included in the confirmation request such as:
POST /v2/transactions/{transactionId}/confirm
📘 Why include Geofencing?
authID already collects geolocation information from the client and stores it in Redis for use in the Identity Portal UI. However, this information is not accessible to customers via API unless explicitly passed at confirmation time.
Providing it yourself ensures:
- Geolocation data is stored in the metadata and not lost
- It becomes accessible for future use cases, including Policy Engine evaluations
- You retain full control over what data is shared
🧱 Example confirm request with Geofencing
confirm request with Geofencing{
"TempId": "9d2806e9-827f-408d-b609-a8de59a94147",
"OperationId": "5bf2938b-2c25-4778-018e-f392e79b24f4",
"Geofencing": {
"LocalTime": "2025-03-20T05:06:13.1490112-04:00",
"Location": {
"Latitude": "14.5",
"Longitude": "14.6"
},
"AdditionalData": [
{
"Key": "OS",
"Value": "iOS"
},
{
"Key": "IP",
"Value": "10.10.10.10"
}
]
},
"Result": 1,
"RejectReason": ""
}
Updated 3 months ago